Introducing FIDO2/WebAuthn support for NodeBB
Ever since the very first commits to the NodeBB codebase, we've made it a point of pride to implement features and functionality that "no other forum has". We wanted to set ourselves apart from other community software offerings by natively supporting new UX paradigms (e.g. single page app, markdown editor, or infinite scrolling), or supporting the latest technologies (e.g. external SSO login, RESTful API) endemic1 to popular web applications. WebAuthn and hardware key support is just the latest in that line of development effort.
Today, I am happy to announce that NodeBB officially supports Multi-factor authentication via hardware keys, built atop the FIDO2/WebAuthn protocol. This functionality was recently added to v3.0 of the Two-Factor Authentication plugin for NodeBB. The plugin already supported a second factor via a time-based one-time password (TOTP), and further support for hardware keys allows users to increase security even more so.
Support for hardware keys via the WebAuthn protocol was sponsored by @yLothar and the mechanical keyboarding community at KEEB.it. Thank you!
What is a hardware key, how is it different from the SMS/one-time password?
You may already be familiar with two-factor authentication used on other sites. Typical implementations include a one-time code sent to you via SMS, or a code generated by a device like your phone.
A nice summary is: 2FA complements the "something you know" aspect of passwords, with "something you have".
However, while a second factor is far and away the best way to further protect your account from password leaks, credential stuffing, or just plain bad password hygiene, there are some known (albeit minor) limitations to both:
- An SMS-based code can be intercepted or your SIM card can be remotely swapped by a compromised agent of the mobile phone carrier
- If a TOTP secret is compromised or leaked, then it can be used and set up by others.
- In both cases, a one-time password is also vulnerable to phishing/social engineering, where a malicious user impersonates the site (e.g. a bank) and asks for your one-time code.
A hardware key is registered with the site and associated with the physical key itself. Short of having your key stolen, it is impossible to impersonate or have its secret revealed via some sort of social engineering attack.
The downside to the hardware key, of course... is that you have to actually buy a hardware key. They're fairly inexpensive, and usable across multiple sites, so it is not an overly burdensome expense, but I'll leave that determination up to you.
How does FIDO2/WebAuthn work in NodeBB?
Much like the existing TOTP support, you are able to register your hardware key from within the user profile page in NodeBB.
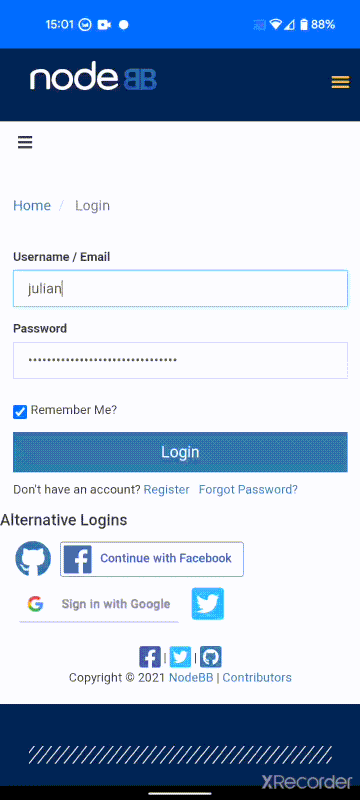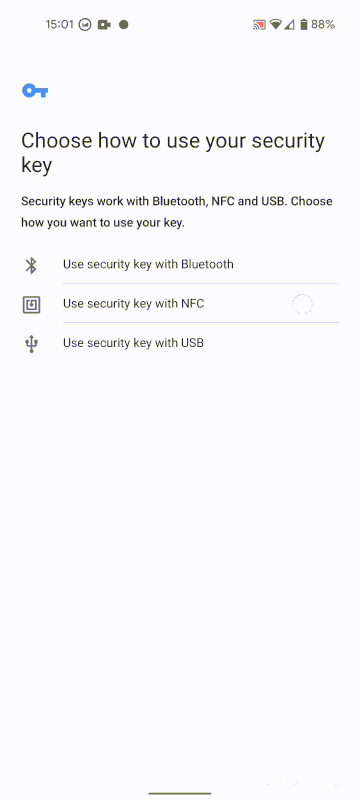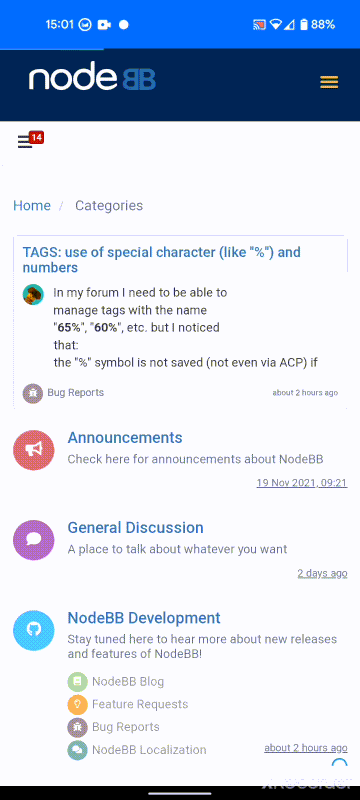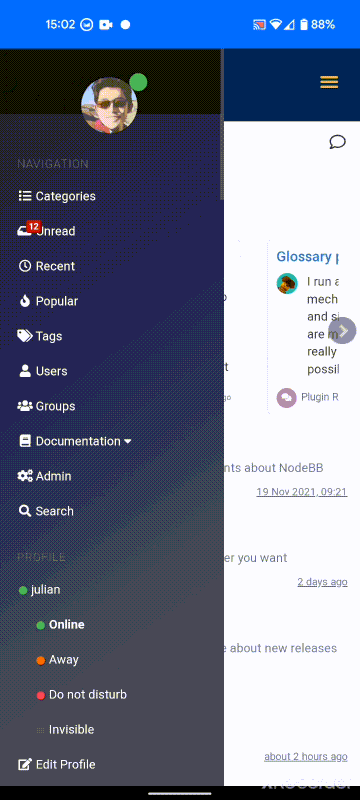
Once the key is registered with your account, whenever you log in, you will be requested to activate your hardware key (usually with some sort of press or tap).
Take a look at it in action on the right. I had already associated the key with my account on my desktop via USB, but am logging into my account on my phone, and completed the challenge using NFC. Neat, isn't it?
How safe is it?
Unless your key is stolen, the hardware key is just as safe as other two-factor authentication methods. As mentioned above, while there are some minor disadvantages to SMS or TOTP-based 2FA, simply having 2FA at all — no matter which method — is the best thing you can do to increase your account security.
Plugin ownership change
Additionally, we have also officially transferred guardianship of the 2factor plugin from my personal account to the NodeBB organization on GitHub, and will bundle it with future versions of NodeBB.
As with all of our bundled plugins, this also automatically means that the plugin is fair game according to our bug bounty.
What's next for the plugin?
Best practice for multi-factor authentication suggests we should enable the ability to associate multiple strategies (e.g. TOTP and hardware key and maybe fingerprint, etc.). Currently, we only support either the hardware key, or the regular QR code token, with backup code support. In future iterations of the plugin, we will be allowing for concurrently registered 2FA methods.
Thanks for reading, and stay safe online! Remember, nobody will ever ask you for your password... or your one-time passcode... and if you use a hardware key, then tell them so and confuse them instead 🙃.
Notes
1 Funny how "endemic" is now a word almost everybody knows the definition of.